Cybersecurity Dynamics: A Foundation for the Science of Cyber Security
I would like to briefly describe the approach that I have been pursuing towards ultimately tackling the holy-grail challenge the research community is confronted with: Building a Foundation for the Science of Cyber Security. The importance of this problem was not widely recognized until the 2008 Science of Security Workshop.
The approach is centered on the novel concept of Cybersecurity Dynamics, which essentially describes the evolution of security state of a cyber system, which is often a very large system (of complex systems). As the term may tell itself, this concept is largely influenced by certain disciplines such as Dynamical System (a field of Applied Mathematics) and Statistical Physics. The evolution of security state is caused by the interaction between the cyber attackers/attacks and the cyber defenders/defenses. While the modeling of Cybersecurity Dynamics is centered on security concepts and domain knowledge, analysis of the resulting models often turns out to be very difficult, due to several technical barriers that I plan to write about at a later time. Nevertheless, the expressive power (if I may abuse the term here) of Cybersecurity Dynamics is amazing: We can build descriptive, prescriptive, predicative, and experimental models surrounding the same concept as well as some natural security metrics that can be derived thereof. It is both interesting and surprising (at least to me) that there are a rich set of mathematical techniques that can address some respective aspects of the problem. So far, I have worked with my mathematician collaborators on several relevant techniques: Stochastic Process, Dynamical System, Statistical Physics, Control Theory, Game Theory, Statistics, and Algebraic Graph Theory. I expect that other mathematical techniques are relevant as well. My vision of the Cybersecurity Dynamics Foundation for the Science of Cybersecurity is depicted in Figure 1.
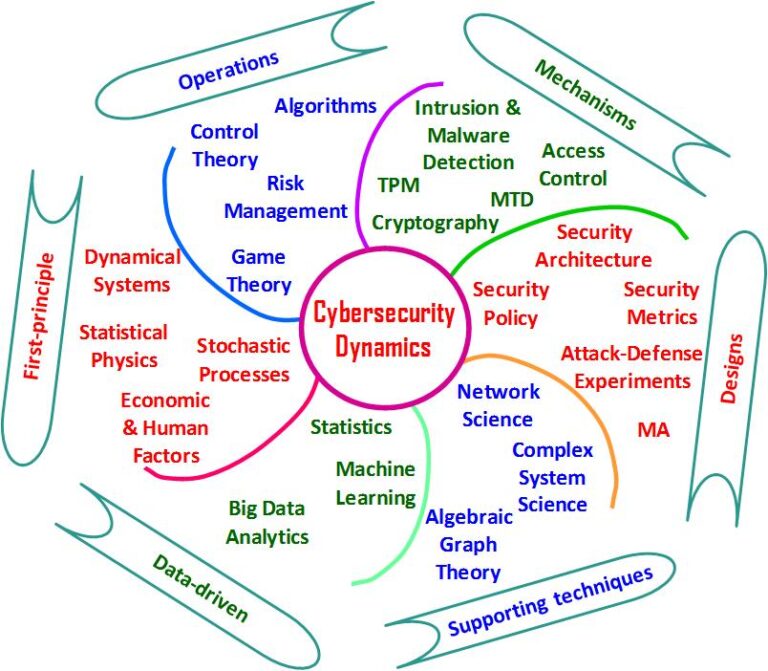
Figure 1. My vision of Cybersecurity Dynamics Foundation for the Science of Cyber Security, where the (sub-)fields mentioned in each perspective are by no means exclusive (explaining the “open-end” in each perspective).
While I firmly believe Cybersecurity Dynamics is the right abstraction that will lead to the ultimately-wanted foundation (i.e., not only deepening our understanding/knowledge, but also guiding the development of tools/instruments for real-life cyber operations risk-management and decision-making), it is also clear to me, as hinted above, that there are a range of challenging theoretic and practical (engineering) problems that must be adequately addressed before we achieve the ultimate goal or fulfill the ambitious vision. Moreover, these problems cannot be bypassed because they are inherent, and therefore must be confronted and tackled — regardless of the specific technical approach that is undertaken. In order to ultimately tackle the holy-grail challenge, there are tons of opportunities for researchers crossing multiple disciplines, crossing multiple sub-disciplines within Computer Science, and crossing the already established various security sub-fields, to closely work together. The way ahead is exciting!!
(Update in May 2016) It has become clear that at a higher-level of abstraction (than Figure 1), Cybersecurity Dynamics offers the following X-Y-Z-t “coordinate system” for exploring cybersecurity, where the X-axis represents first-principle modeling (i.e., assumption-driven modeling), the Y-axis represents data analitics (i.e., data-driven analysis), the Z-axis represents security metrics, and t means that everything is dynamic. This is highlighted in Figure 2 below
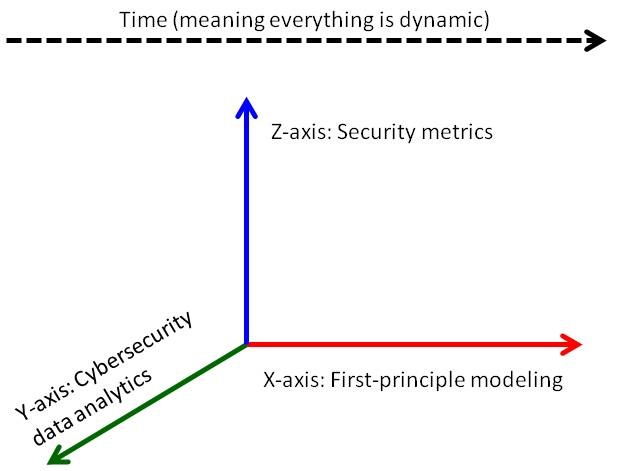
Figure 2. The X-Y-Z-t “coordinate system” for exploring cybersecurity.
Manuscripts in submission:
- Brandon Collins, Shouhuai Xu, Philip Brown. A Coupling Approach to Analyzing Games with Dynamic Environments. In submission.
- Brandon Collins, Shouhuai Xu, Philip Brown. SoK: Game-Theoretic Cybersecurity: Assumptions, Models, Gaps, and Bridges. In submission.
- Z. Li, J. Tang, D. Zou, Q. Chen, S. Xu, C. Zhang, Y. Li, and H Jin. Towards Making Deep Learning-based Vulnerability Detectors Robust. In submission.
Published/accepted papers:
- (new) Zhen Li, Ning Wang, Deqing Zou, Yating Li, Ruqian Zhang, Shouhuai Xu, Chao Zhang, and Hai Jin. On the Effectiveness of Function-Level Vulnerability Detectors for Inter-Procedural Vulnerabilities, Proceedings of International Conference on Software Engineering (ICSE’2024)
- (new) Theodore Longtchi. Characterizing Internet-Based Social Engineering Attacks through a Psychological Lens. PhD Dissertation. July 2024.
- (new) Jose Luis Castanon Remy, Ekzhin Ear, and Shouhuai Xu. Quantifying and Reducing System Non-Resilience: Methodology, Metrics, and Case Study. Invited Book Chater to appear in 2024/2025.
- (new) J. Turner, S. Li, and S. Xu. Jamming-Resistant Communications via Cryptographic Secret Sharing, IEEE International Conference on Communications 2024 (ICC’2024)
- (new) Xiaoyu Zhang, Maochao Xu and Shouhuai Xu. Smart Home Cyber Insurance Pricing, Proceedings of International Science of Cyber Security (SciSec’2024).
- (new) Theodore Longtchi and Shouhuai Xu. Characterizing the Evolution of Psychological Factors Exploited by Malicious Emails, Proceedings of International Science of Cyber Security (SciSec’2024).
- (new) Theodore Longtchi and Shouhuai Xu. Characterizing the Evolution of Psychological Tactics and Techniques Exploited by Malicious Emails, Proceedings of International Science of Cyber Security (SciSec’2024).
- (new) Eric Ficke, Raymond Bateman and Shouhuai Xu. AutoCRAT: Automatic Cumulative Reconstruction of Alert Trees, Proceedings of International Science of Cyber Security (SciSec’2024).
- (new) Theodore Longtchi, Rosana Rodriguez, Laith Al-Shawaf, Adham Atyabi, and Shouhuai Xu. Internet-based Social Engineering Psychology, Attacks, and Defenses: A Survey. Proceedings of IEEE, 112(3):210-246 (2024).
- (new) Logan Zeien, Caleb Chang, Ekzhin Ear, and Shouhuai Xu. Characterizing Advanced Persistent Threats Through the Lens of Cyber Attack Flows. Military Cyber Affairs Journal, Volume 7, Issue 1 , Article 5. Paper available at here.
- (new) H. Zhang, J. Peng, J. Mao, and S. Xu. Repeated Data Breaches and Executive Compensation. Applied Economics Letters, Accepted on December 12, 2023
- (new) Shuai Li, Alessio Baiocco, and Shouhuai Xu. Characterizing Privacy Risks in Healthcare IoT Systems, Proceedings of the First International Workshop Secure and Resilient Digital Transformation of Healthcare (SUNRISE’2023), November 30, 2023
- E. Ear, J. Remy, A. Feffer, and S. Xu. Characterizing Cyber Attacks against Space Systems with Missing Data: Framework and Case Study. Accepted to 2023 IEEE Conference on Communications and Network Security (IEEE CNS’2023).
- J. Peng, H. Zhao, J. Mao, and S. Xu. How do repeated data breaches affect firm policies? Accepted to Applied Economics Letters.
- Z. Li, R. Zhang, D. Zou, N. Wang, Y. Li, S. Xu, C. Chen, H. Jin. Robin: A Novel Method to Produce Robust Interpreters for Deep Learning-Based Code Classifiers. The 38th IEEE/ACM International Conference on Automated Software Engineering (ASE’2023).
- K. Paarporn and S. Xu. Analysis of Contagion Dynamics with Active Cyber Defenders. The 62nd IEEE Conference on Decision and Control (CDC’2023)
- Z. Sun, M. Xu, K. Schweitzer, R. Bateman, A. Kott, and S. Xu. Cyber Attacks against Enterprise Networks: Characterization, Modelling and Forecasting. The 5th International Conference on Science of Cyber Security (SciSec’2023).
- M. Zaman, L. Tao, M. Maldonado, C. Liu, A. Sunny, S. Xu and L. Chen. Optimally Blending Honeypots into Production Networks: Hardness and Algorithms. The 5th International Conference on Science of Cyber Security (SciSec’2023).
- R. Rodriguez, T. Longtchi, K. Gwartney, E. Ear, D. Azari, C. Kelly and S. Xu. Quantifying Psychological Sophistication of Malicious Emails. The 5th International Conference on Science of Cyber Security (SciSec’2023).
- Qi Xia, Qian Chen, and Shouhuai Xu. Near-Ultrasound Inaudible Trojan (NUIT): Exploit your speaker to Attack your Voice-Controllable Devices. Usenix Security’2023, to appear.
- L. Tao, L. Chen, L. Xu, S. Xu, Z. Gao, and W. Shi. Electoral manipulation via influence: probabilistic model. Auton. Agents Multi Agent Syst. 37(1): 18(2023)
- D. Li, S. Cui, Y. Li, J. Xu, F. Xiao, and S. Xu. PAD: Towards Principled Adversarial Malware Detection Against Evasion Attacks. IEEE Transactions on Dependable and Secure Computing, accepted.
- E. Ear, J. Remy, and S. Xu. Towards Automated Cyber Range Design: Characterizing and Matching Demands to Supplies. IEEE International Conference on Cyber Security and Resilience (CSR’2023).
- Jin Peng, Haofei Zhang, Juan Mao, and Shouhuai Xu. Repeated data breaches and firm value. Economics Letters, 2023.
- Shouhuai Xu. AICA Development Challenges. Book Chapter in “Building an Artificial Intelligent Cyber-defense Agent”, to appear in 2023
- Azizeh K. Sowan, Nancy Staggers, Charles C. Reed, Tommye Austin, Qian Chen, Shouhuai Xu, and Emme Lopez. State of Science in Alarm System Safety: Implications for Researchers, Vendors, and Clinical Leaders. Biomedical Instrumentation & Technology. (56)1 pp 19-28, 2022. https://doi.org/10.2345/0899-8205-56.1. AAMI Best Research Article Award.
- Rosana Montanez Rodriguez, Adham Atyabi, and Shouhuai Xu. Social Engineering Attacks and Defenses in the Physical World vs. Cyberspace A Contrast Study. Book Chapter in “Cybersecurity and Cognitive Science”, 2022, pages 3-41.
- Haoyu Chen, Deqing Zou, Hai Jin, Shouhuai Xu, and Bin Yuan. SAND: semi-automated adaptive network defense via programmable rule generation and deployment. Science China Information Sciences 65(7): 1-18 (2022)
- Mir Mehedi Ahsan Pritom and Shouhuai Xu. Supporting Law-Enforcement to Cope with Blacklisted Websites: Framework and Case Study. Proc. of the 2022 IEEE Conference on Communications and Network Security (CNS’2022), pp 181-189.
- Nathan Daughety, Marcus Pendleton, Rebeca Perez, Shouhuai Xu, and John Franco. Auditing a Software-Defined Cross Domain Solution Architecture. Proc. of the 2022 IEEE International Conference on Cyber Security and Resilience (CSR’2022), pp 96-103
- Eric Ficke, Raymond M. Bateman, and Shouhuai Xu. Reducing Intrusion Alert Trees to Aid Visualization. Proc. of the 2022 International Conference on Network and System Security (NSS’2022): pp 140-154
- Joshua H. Seaton, Sena Hounsinou, Timothy Wood, Shouhuai Xu, Philip N. Brown, and Gedare Bloom. Poster: Toward Zero-Trust Path-Aware Access Control. Proc. of SACMAT’2022: pp 267-269
- Rosana Montanez Rodriguez and Shouhuai Xu. Cyber Social Engineering Kill Chain. Proc. of the 2022 International Conference on Science of Cyber Security (SciSec’2022): pp 487-504
- Mir Pritom, Defending Against Malicious Websites: Themed Threats, Detection, and Law-Enforcement. PhD Dissertation. July 2022.
- Eric Ficke, Reconstructing Alert Trees for Cyber Triage. PhD Dissertation. April 2022.
- (J. Shi, D. Zou, S. Xu, X. Deng, and H. Jin. Does OpenBSD and Firefox’s Security Improve with Time?, accepted to IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), to appear
- S. He, E. Ficke, M. Pritom, H. Chen, Q. Tang, Q. Chen, M. Pendleton, L. Njilla, and S. Xu. Blockchain-Based Automated and Robust Cyber Security Management, accepted to Journal of Parallel and Distributed Computing (JPDC)
- Z. Li, Q. Chen, C. Chen, Y. Zou and S. Xu. RoPGen: Towards Robust Code Authorship Attribution via Automatic Coding Style Transformation. International Conference on Software Engineering (ICSE’2022).
- Huashan Chen. A Framework for Quantifying Security Effectiveness of Cyber Defenses, PhD Dissertation. Oct. 2021.
- Rosana Montanez Rodriguez, Adham Atyabi, and Shouhuai Xu. Social Engineering Attacks and Defenses in the Physical World vs. Cyberspace A Contrast Study. Invited Book Chapter to “Cybersecurity and Cognitive Science”, 2021.
- Brandon Collins, Shouhuai Xu, and Philip Brown. Paying Firms to Share Cyber Threat Intelligence. GameSec’2021.
- Nathan Daughety, Marcus Pendleton, Shouhuai Xu, Laurent Njilla, and John Franco. vCDS: A Virtualized Cross Domain Solution Architecture. Milcom’2021.
- D. Li, Q. Li, Y. Ye, and S. Xu. Arms Race in Adversarial Malware Detection: A Survey. Accepted to ACM Computing Survey, 2021.
- D. Li, T. Qiu, S. Chen, Q. Li, and S. Xu. Can We Leverage Predictive Uncertainty to Detect Dataset Shift and Adversarial Examples in Android Malware Detection? ACSAC’2021
- H. Chen, H. Cam, and S. Xu. Quantifying Cybersecurity Effectiveness of Dynamic Network Diversity. accepted to IEEE Transactions on Dependable and Secure Computing, 2021.
- L. Chen, A. Sunny, L. Xu, S. Xu, Z. Gao, Y. Lu, W. Shi, and N. Shah. Computational Complexity Characterization of Protecting Elections from Bribery. Accepted to Theoretical Computer Science, 2021
- S. Xu. SARR: A Cybersecurity Metrics and Quantification Framework (Keynote Address). The 3rd International Conference on Science of Cyber Security (SciSec’2021).
- J. Charlton, P. Du, and S. Xu. A New Method for Inferring Ground-Truth Labels and Malware Detector Effectiveness Metrics. The 3rd International Conference on Science of Cyber Security (SciSec’2021).
- S. Xu, M. Yung, and J. Wang. Seeking Foundations for the Science of Cyber Security. Information Systems Frontiers 23 (2), 263-267
- L. Tao, L. Chen, L. Xu, S. Xu, Z. Gao, W. Shi and D. Huang. Hardness and Algorithms for Electoral Manipulation under Media Influence. The 15th Frontiers of Algorithmics Workshop, 2021.
- V. Trieu-Do, R. Garcia-Lebron, M. Xu, S. Xu, and Y. Feng. Characterizing and Leveraging Granger Causality in Cybersecurity: Framework and Case Study. EAI Endorsed Transactions on Security and Safety 7 (25), e4
- Z. Li, D. Zou, S. Xu, Z. Chen, Y. Zhu, and H. Jin. VulDeeLocator: A Deep Learning-based Fine-grained Vulnerability Detector. In IEEE Transactions on Dependable and Secure Computing (TDSC), 2021.
- John Charlton. Inferring Malware Detector Metrics in the Absence of Ground-Truth, PhD Dissertation. April 2021.
- Q. Chen, P. Romanowich, J. Castillo, K. Roy, G. Chavez, and S. Xu. ExHPD: Exploiting Human, Physical and Driving Behaviors to Detect Vehicle Cyber Attacks. IEEE Internet of Things Journal, 2021
- Y. Han, W. Lu, and S. Xu. Preventive and Reactive Cyber Defense Dynamics with Ergodic Time-dependent Parameters Is Globally Attractive. IEEE Transactions on Network Science and Engineering (TNSE), 2021.
- Z. Fang, M. Xu, S. Xu, and T. Hu. A Framework for Predicting Data Breach Risk: Leveraging Dependence to Cope with Sparsity. IEEE Transactions on Information Forensics & Security (T-IFS). 16, 2186-2201
- D. Li, Q. Li, Y. Ye, and S. Xu. Enhancing Deep Neural Networks Against Adversarial Malware Examples. IEEE Transactions on Network Science and Engineering (TNSE), accepted for publication, 2021.
- Z. Li, D. Zou, S. Xu, H. Jin, Y. Zhu, Z. Chen, S. Wang, and J. Wang. SySeVR: A Framework for Using Deep Learning to Detect Software Vulnerabilities. IEEE Transactions on Dependable and Secure Computing (TDSC), accepted for publication, 2021.
- D. Zou, Y. Zhu, S. Xu, Z. Li, H. Jin, and H. Ye. Interpreting Deep Learning-based Vulnerability Detector Predictions Based on Heuristic Searching. ACM Transactions on Software Engineering and Methodology (ACM TOSEM), accepted, 2020.
- Z. Fang, P. Zhao, M. Xu, S. Xu, T. Hu, and X. Fang. Statistical Modeling of Computer Malware Propagation Dynamics in Cyberspace. Journal of Applied Statistics. Accepted, 2020.
- Mir Mehedi Ahsan Pritom, Kristin Schweitzer, Raymond Bateman, Min Xu and Shouhuai Xu. Data-Driven Characterization and Detection of COVID-19 Themed Malicious Websites. IEEE ISI’2020.
- Mir Mehedi Ahsan Pritom, Kristin Schweitzer, Raymond Bateman, Min Xu and Shouhuai Xu. Characterizing the Landscape of COVID-19 Themed Cyberattacks and Defenses. IEEE ISI’2020.
- Eric Ficke and Shouhuai Xu. APIN: Automatic Attack Path Identification in Computer Networks. IEEE ISI’2020.
- Z. Liu, R. Zheng, W. Lu, and S. Xu. Using Event-Triggered Control to Estimate Cybersecurity Equilibria. IEEE/CAA Journal of Automatica Sinica, accepted, 2020.
- S. Xu. The Cybersecurity Dynamics Way of Thinking and Landscape (Invited Paper). ACM Workshop on Moving Target Defense (MTD’2020).
- R. Rodriguez, E. Golob, and S. Xu. Human Cognition through the Lens of Social Engineering Cyberattacks. Frontiers in Psychology, 2020.
- Y. Zhang, Y. Fan, S. Hou, Y. Ye, X. Xiao, P. Li, C. Shi, L. Zhao, S. Xu. Cyber-guided Deep Neural Network for Malicious Repository Detection in GitHub. IEEE International Conference on Knowledge Graph (ICKG’2020).
- L. Chen, A. Sunny, L. Xu, S. Xu, Z. Gao, Y. Lu, W. Shi, and N. Shah. Computational complexity characterization of protecting elections from bribery. International Computing and Combinatorics Conference (COCOON), 85-97, 2020.
- H. Chen, M. Pendleton, L. Njilla, and S. Xu. A Survey on Ethereum Systems Security: Vulnerabilities, Attacks and Defenses. ACM Computing Surveys (CSUR) 53 (3), 1-43.
- P. Romanowich, Q. Chen, and S. Xu. Relationships between Driver Errors and Delay Discounting in a Simulated Driving Task. Perspectives on Behavior Science, to appear, 2020.
- D. Zou, S. Wang, S. Xu, Z. Li, and H. Jin. muVulDeePecker: A Deep Learning-Based System for Multiclass Vulnerability Detection. IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), 2019, to appear.
- L. Chen, L. Xu, S. Xu, Z. Gao, and W. Shi. Election with Bribe-Effect Uncertainty: A Dichotomy Result. Proceedings of the 28th International Joint Conference on Artificial Intelligence (IJCAI’2019)
- Y. Fan, Y. Zhang, S. Hou, L. Chen, Y. Ye, C. Shi, L. Zhao, and S. Xu. iDev: Enhancing Social Coding Security by Cross-platform User Identification Between GitHub and Stack Overflow. Proceedings of the 28th International Joint Conference on Artificial Intelligence (IJCAI’2019)
- Z. Lin, W. Lu, and S. Xu. Unified Preventive and Reactive Cyber Defense Dynamics Is Still Globally Convergent. IEEE/ACM Transactions on Networking, 2019, to appear. Note: This paper unifies two widely-studied classes of cybersecurity dynamic models into a single framework and proves the resulting generalized dynamics is globally convergent.
- Eric Ficke, Kristin M. Schweitzery, Raymond M. Batemany, and Shouhuai Xu. Analyzing Root Causes of Intrusion Detection False-Negatives: Methodology and Case Study. IEEE Milcom 2019.
- Gabriel C. Fernandez and Shouhuai Xu. A Case Study on Using Deep Learning for Network Intrusion Detection. IEEE Milcom 2019.
- Lingwei Chen, Shifu Hou, Yanfang Ye, Thirimachos Bourlai, Shouhuai Xu and Liang Zhao. iTrustSO: An Intelligent System for Automatic Detection of Insecure Code Snippets in Stack Overflow. The Fourth International Workshop on Social Network Analysis Surveillance Technologies (SNAST 2019), In Proc. IEEE/ACM 2019 International Conference on Advances in Social Networks Analysis and Mining (ASONAM 2019).
- Richard Garcia Lebron, A Framework for Characterizing Cyber Attack Reconnaissance Behaviors, PhD Dissertation, July 2019.
- G. Fernandez, Deep Learning Approaches for Network Intrusion Detection, MS Thesis, UTSA, May 2019.
- X. Fang, M. Xu, S. Xu and P. Zhao. A deep learning framework for predicting cyber attacks rates, EURASIP Journal on Information Security, to appear
- J. Mireles, E. Ficke, J. Cho, P. Hurley, and S. Xu. Metrics Towards Measuring Cyber Agility. IEEE Transactions on Information Forensics & Security, 2019.
- D. Li, Q. Li, Y. Ye, and S. Xu. Enhancing Robustness of Deep Neural Networks Against Adversarial Malware Samples: Principles, Framework, and AICS’2019 Challenge. AAAI-19 Workshop on Artificial Intelligence for Cyber Security (AICS’2019). (Challenge Winner)
- L. Chen, L. Xu, S. Xu, Z. Gao, and W. Shi. Election with Bribed Voter Uncertainty: Hardness and Approximation Algorithm. AAAI’2019.
- R. Garcia-Lebron, D. Myers, S. Xu, and J. Sun. Node Diversification in Complex Networks by Decentralized Coloring. Journal of Complex Networks, 2018
- J. Cho, S. Xu, P. Hurley, M. Mackay, T. Benjamin, and M. Beaumont. STRAM: Measuring the Trustworthiness of Computer-based Systems. Appendix to the paper is here. ACM Computing Survey, accepted, 2018.
- Y. Ye, S. Hou, L. Chen, X. Li, L. Zhao, S. Xu, J. Wang, Q. Xiong. ICSD: An Automatic System for Insecure Code Snippet Detection in Stack Overflow over Heterogeneous Information Network, ACSAC’2018, to appear.
- L.Chen, S. Hou, Y. Ye, and S. Xu. DroidEye: Fortifying Security of Learning-based Classifier against Adversarial Android Malware Attacks. In Proc. IEEE/ACM 2018 International Conference on Advances in Social Networks Analysis and Mining (ASONAM 2018).
- S. Xu. Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. A book chapter to appear in Springer book entitled Proactive and Dynamic Network Defense, 2018.
- E. Ficke, K. Schweitzer, R. Bateman, and S. Xu. Characterizing the Effectiveness of Network-based Intrusion Detection Systems, IEEE Milcom 2018.
- R. Garcia-Lebron, K. Schweitzer, R. Bateman, and S. Xu. A Framework for Characterizing the Evolution of Cyber Attacker-Victim Relation Graphs, IEEE Milcom 2018.
- J. Charlton, J. Cho, and S. Xu. Measuring Relative Accuracy of Malware Detectors in the Absence of Ground Truth, IEEE Milcom 2018.
- M. Xu, K. Schweitzer, R. Bateman, and S. Xu. Modeling and Predicting Cyber Hacking Breaches. IEEE Transactions on Information Forensics & Security, 13(11): 2856-2871 (2018).
- P. Du, Z. Sun, H. Chen, J. Cho, and S. Xu. Statistical Estimation of Malware Detection Metrics in the Absence of Ground Truth. IEEE Transactions on Information Forensics & Security, 13(12): 2965-2980 (2018).
- H. Chen, J. Cho, and S. Xu. Quantifying the Security Effectiveness of Firewalls and DMZs. 2018 Symposium and Bootcamp on the Science of Security (HotSoS’18), 2018.
- H. Chen, J. Cho, and S. Xu. Poster: Quantifying the security effectiveness of network diversity. 2018 Symposium and Bootcamp on the Science of Security (HotSoS’18), 2018.
- C. Peng, M. Xu, S. Xu, and T. Hu. Modeling Multivariate Cybersecurity Risks. Journal of Applied Statistics, Accepted, 2018.
- Zhen Li, Deqing Zou, Shouhuai Xu, Xinyu Ou, Hai Jin, Sujuan Wang, Zhijun Deng, Yuyi Zhong. VulDeePecker: A Deep Learning-Based System for Vulnerability Detection. Network and Distributed System Security Symposium 2018 (NDSS’18). Note: The two databases we created in this paper, are publicly available at GitHub here.
- R. Zheng, W. Lu, and S. Xu. Preventive and Reactive Cyber Defense Dynamics Is Globally Stable. IEEE Transactions on Network Science and Engineering. Note: This paper settles down an almost 10 years old open problem by proving that this particular kind of cybersecurity dynamics is globally convergent in the entire parameter universe.
- Marcus Pendleton. System Call Anomaly Detection in Multi-threaded Programs, PhD Thesis, Nov. 2017
- M. Pendleton and S. Xu. A Dataset Generator for Next Generation System Call Host Intrusion Detection Systems. Proceedings of Milcom’2017.
- M. Saleh, P. Ratazzi, and S. Xu. A Control Flow Graph-based Signature for Packer Identification. Proceedings of Milcom’2017.
- A. Tyra, Jingtao Li, Y. Shang, S. Jiang, Y. Zhao, and S. Xu. Robustness of non-interdependent and interdependent networks against dependent and adaptive attacks. Physica A 482 (2017) 713-727.
- H. Chen, X. Zhao, F. Liu, S. Xu, and W. Lu. Optimizing inter-connections to maximize the spectral radius of interdependent networks. Physical Review E, Vol.95, No.3; DOI: 10.1103/PhysRevE.95.032308.
- M. Xu, L. Hua, and S. Xu. A Vine Copula Model for Predicting the Effectiveness of Cyber Defense Early-Warning. Technometrics, 2017. (Local copy)
- C. Peng, M. Xu, S. Xu, and T. Hu. Modeling and Predicting Extreme Cyber Attack Rates via Marked Point Processes. Journal of Applied Statistics, 2017. (Local copy). This paper is one of the two Highly Commended Finalists for the Best Paper Prize among ALL of the papers published in the Journal of Applied Statistics in year 2017!
- J. Mireles. Modeling and Analyzing Cyber Adaptations and Attack Narratives. MS Thesis, 2017.
- X. Hu, M. Xu, S. Xu, and P. Zhao. Multiple Cyber Attacks against a Target with Observation Errors and Dependent Outcomes: Characterization and Optimization, Reliability Engineering & System Safety, 2017.
- M. Pendleton, R. Garcia-Lebron, J. Cho, and S. Xu. A Survey on Systems Security Metrics, ACM Computing Survey, 2017. Note: The ontologies accommodating the metrics described in the paper are available at GitHub here. We hope this is a starting point of community effort that eventually will achieve the ultimate goal. An earlier draft without considering ontology: A Survey on Security Metrics.
- Z. Li, D. Zou, S. Xu, H. Jin, H. Qi, and J. Hu. VulPecker: An Automated Vulnerability Detection System Based on Code Similarity Analysis. ACSAC’2016. Note: The two databases we created in this paper, namely the Vulnerability Patch Database and the Vulnerability Code Instance Database, are publicly available at GitHub here. We hope the databases will evolve as more vulnerability information becomes available in the future, which would take a community effort.
- J. Mireles, J. Cho, and S. Xu. Extracting Attack Narratives from Traffic Datasets. The 1st International Conference on Cyber Conflict in the U.S. (CyCon U.S. ‘2016).
- J. Cho, P. Hurley, and S. Xu. Metrics and Measurement of Trustworthy Systems. Milcom’2016.
- G. Da, M. Xu and S. Xu. On the Quasi-Stationary Distribution of SIS Models. Probability in the Engineering and Informational Sciences, Volume 30, Issue 4, October 2016, pages 622-639.
- Z. Zhan, M. Xu, and S. Xu. Predicting Cyber Attack Rates with Extreme Values. IEEE Transactions on Information Forensics & Security, 10(8): 1666-1677 (2015).
- Y. Chen, Z. Huang, S. Xu and Y. Lai. Spatiotemporal patterns and predictability of cyberattacks. PLoS One 10(5): e0124472. oi:10.1371/journal.pone.0124472, 2015.
- R. Zheng, W. Lu, and S. Xu. Active Cyber Defense Dynamics Exhibiting Rich Phenomena. 2015 Symposium and Bootcamp on the Science of Security (HotSoS’15).
- Z. Zhan, M. Xu, and S. Xu. A Characterization of Cybersecurity Posture from Network Telescope Data. Proceedings of The 6th International Conference on Trustworthy Systems (InTrust’14).
- L. Xu, Z. Zhan, S. Xu, and K. Ye. An Evasion and Counter-Evasion Study in Malicious Websites Detection. IEEE 2014 Conference on Communications and Network Security (IEEE CNS’14).
- L. Xu. Detecting and Characterizing Malicious Websites. PhD Thesis, 2014.
- Z. Zhan. A Statistical Framework for Analyzing Cyber Threats. PhD Thesis, 2014.
- Y. Han, W. Lu and S. Xu. Characterizing the Power of Moving Target Defense via Cyber Epidemic Dynamics. 2014 Symposium and Bootcamp on the Science of Security (HotSoS’14). The slides are available here.
- G. Da, M. Xu and S. Xu. A New Approach to Modeling and Analyzing Security of Networked Systems. 2014 Symposium and Bootcamp on the Science of Security (HotSoS’14). The slides are available here.
- S. Xu. Cybersecurity Dynamics (poster). 2014 Symposium and Bootcamp on the Science of Security (HotSoS’14). The poster slide is available here.
- S. Xu. Emergent Behavior in Cybersecurity (poster). 2014 Symposium and Bootcamp on the Science of Security (HotSoS’14). The poster slide is available here.
- M. Xu, G. Da, and S. Xu. Cyber Epidemic Models with Dependencies. Internet Mathematics, 11:1, 62-92. This paper won Taylor & Francis Mathematics & Statistics Readers’ Award in Year 2015
- S. Xu, W. Lu, L. Xu, and Z. Zhan. Adaptive Epidemic Dynamics in Networks: Thresholds and Control. ACM Transactions on Autonomous and Adaptive Systems (TAAS), 8(4), Article 19, 2014.
- W. Lu, S. Xu, and X. Yi. Optimizing Active Cyber Defense. The 4th Conference on Decision and Game Theory for Security (GameSec’13), pp 206-225.
- S. Xu, W. Lu, and H. Li, A Stochastic Model of Active Cyber Defense Dynamics. Internet Mathematics, 11:1, 23-71.
- Z. Zhan, M. Xu, and S. Xu. Characterizing Honeypot-Captured Cyber Attacks: Statistical Framework and Case Study. IEEE Transactions on Information Forensics & Security (IEEE TIFS), 8(11): 1775-1789, (2013).
- M. Xu and S. Xu. An Extended Stochastic Model for Quantitative Security Analysis of Networked Systems. Internet Mathematics, 8(3): 288-320 (2012).
- S. Xu, W. Lu, and Z. Zhan. A Stochastic Model of Multi-Virus Dynamics. IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), 9(1): 30-45 (2012).
- S. Xu, W. Lu, and L. Xu. Push- and Pull-based Epidemic Spreading in Networks: Thresholds and Deeper Insights. ACM Transactions on Autonomous and Adaptive Systems (TAAS), 7(3): Article 32 (2012).
- X. Li, P. Parker, and S. Xu. A Stochastic Model for Quantitative Security Analysis of Networked Systems. IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), 8(1): 28-43 (2011).
- Y. Shang, W. Luo, and S. Xu. L-hop percolation on networks with arbitrary degree distributions and its applications. Physical Review E 84, 031113 (2011).
- S. Xu. Towards a Theoretical Framework for Trustworthy Cyber Sensing. Proceedings of the 2010 SPIE Conference on SPIE Defense, Security, and Sensing (DSS’10).
- S. Xu. Collaborative Attack vs. Collaborative Defense. Invited Paper in the Proceedings of The 4th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborativeCom’08), Nov. 13-16, 2008.
- X. Li and S. Xu. A stochastic modeling of coordinated internal and external attacks. Manuscript.
Keynote/Invited/Colloquium/Seminar/Panel Talks:
- Adaptive Security Dynamics in Critical and Healthcare Sectors. Norwegian Computing Center/Norsk Regnesentral, August 6, 2024.
- Adaptive Cyber Defense: From Theory to Practice with Applications to Healthcare Infrastructures, Norwegian Computing Center/Norsk Regnesentral, August 2, 2024.
- CR2M: Cyber Risks to Missions Management: Framework, Techniques, and Prototype, National Defense University, June 6, 2024.
- Making Space Infrastructures and Systems Resilient against Cyber Attacks. US Space Force University Consortium Symposium, June 5, 2024.
- Cybersecurity Dynamics: A Foundation Enabling Automated and Autonomous Cyber Operations & Risk Management. USCYBERCOM Academic Engagement Network (AEN) Tech Talk Series. May 8, 2024.
- Secure Space Situational Awareness, USSPACECOM AEE 2024 Spring Symposium, April 12, 2024
- Satellite Cybersecurity Vulnerabilities, Attacks, and Defenses, USSPACECOM AEE 2024 Spring Symposium, April 12, 2024.
- UCCS Space Cybersecurity and Mission Assurance Research. USSPACECOM AEE 2024 Spring Symposium, April 12, 2024.
- Cybersecurity Metrics. Goethe University Frankfurt, Germany, December 13, 2023
- Cyber Threats Forecasting. Nanjing University of Posts and Communications, China, December 10, 2023
- CR2M: Cyber Risks to Missions Management: Framework, Techniques, and Prototype, National Defense University, December 6, 2023
- UCCS Cybersecurity Research: Vision, Example Results, and Future Research Directions, Fort Carson, November 15, 2023
- Making Space Infrastructures and Systems Resilient against Cyber Threats: Vision, Framework, Ongoing Research, and Future Directions. UCCS Mountain Lion Club, November 8, 2023
- Making Space Infrastructures and Systems Resilient against Cyber Threats: Vision, Framework, Ongoing Research, and Future Directions. AFRL/RV Space Cyber Summit 2023, October 12, 2023
- Robotics, AI and Cybersecurity, TechnoWizards Robotics Summer Camp, June 6, 2023
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Ohio State University, April 27, 2023
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. University of Missouri Kansas City, Feb 17, 2023
- Repeated Data Breaches and Firm Value, The 18th Annual Forum on Financial Information Systems and Cybersecurity: A Public Policy Perspective, University of Maryland College Park, January 11, 2023
- Towards Quantitative Cyber Risk Management. Curiosity Unlimited, Dec. 9, 2022.
- CR2M2: A Framework for Cyber Risks to Missions Management, National Defense University, Nov 16, 2022.
- Path-Aware Risk Scores for Access Control in Zero-Trust Systems, Presentation at CAE in Cybersecurity Symposium, June 9, 2022.
- Towards Quantifying Cybersecurity, University of Central Florida, March 31, 2022
- Impact of COVID-19 on Corporate Cybersecurity, The 17th Annual Forum on Financial Information Systems and Cybersecurity: A Public Policy Perspective, University of Maryland College Park, March 25, 2022
- Space Foundation Symposium 365 Panel on “Redefining the Digital World Around Us”, March 9, 2022
- SARR: A Cybersecurity Metrics and Quantification Framework. CAE Forum, Oct. 6, 2021.
- SARR: A Cybersecurity Metrics and Quantification Framework. SciSec’2021 Keynote, Aug. 14, 2021.
- Cybersecurity Metrics and Quantification: Problems, Some Results, and Research Directions. The Defense and Aerospace Test and Analysis Workshop (DataWorks’2021), April 12, 2021.
- Cybersecurity and Robotics (Outreach Talk), TechnoWizards, November 8, 2020.
- Towards A Systematic Framework for Agile Cyber Defense Decision-Making with Trustworthiness / Uncertainty Quantification. Intelligent Fusion Technology, Inc. October 6, 2020.
- Towards A Systematic Framework for Agile Cyber Defense Decision-Making with Trustworthiness / Uncertainty Quantification. UTSA National Security Collaboration Center, Sept. 24, 2020.
- Towards A Systematic Framework for Agile Decision Making with Trustworthiness Quantification. Briefing to Army Science Board, July 16, 2020.
- Cybersecurity Dynamics: A Metrics-Driven Framework for Cybersecurity Quantification. U.S. National Institute of Standards and Technology, January 7, 2020.
- Cybersecurity Dynamics: Framework, Some Results, and Future Research Directions. Old Dominio University, November 13, 2019.
- Cybersecurity Dynamics: Framework, Some Results, and Future Research Directions. Nankai University, August 13, 2019.
- New Progresses in Cybersecurity Dynamics. Nanjing University, August 12, 2019.
- Cybersecurity Dynamics: Framework, Some Results, and Future Research Directions. Zhejiang University, August 7, 2019.
- Cybersecurity Dynamics: Framework, Some Results, and Future Research Directions. Center for Secure Information Systems, George Mason University, April 22, 2019.
- Cybersecurity Dynamics Overview. The 15th Annual Cybersecurity Forum on Financial Information Systems and Cybersecurity: A Public Policy Perspective. Smith School of Business and School of Public Policy, University of Maryland College Park, January 9, 2019.
- Cybersecurity Data Analytics: Problems, Some Results, and Research Directions. Department of Statistics, University of Texas at San Antonio, September 14, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. University of Science and Technology of China, August 17, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Tutorial at SciSec’2018, August 12, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Xi’an JiaoTong University University, August 9, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity (Part B). Xi’an University of Posts and Telecommunications University, August 8, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity (Part A). Shaanxi Normal University, August 8, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Tsinghua University, August 6, 2018.
- Cybersecurity-Oriented Statistics: Problems, Some Results, and Research Directions. School of Mathematics and Statistics, Jiangsu Normal University, July 15, 2018.
- Cybersecurity-Oriented Statistics: Problems, Some Results, and Research Directions. School of Statistics and Data Science, July 12, 2018.
- Cybersecurity Dynamics: New Progresses. Nanjing University of Posts and Telecommunications, July 11, 2018.
- Cybersecurity Dynamics: New Progresses. Chongqing University, July 9, 2018.
- Cybersecurity Dynamics: New Progresses. Wuhan University, July 5, 2018.
- Cybersecurity Dynamics: New Progresses. Huazhong University of Science and Technology, July 4, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Fudan University, June 29, 2018.
- Cybersecurity Dynamics: New Progresses. East China Normal University, June 28, 2018.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. North Carolina State University, April 10, 2018.
- Cybersecurity Dynamics: Recent Progresses. Huazhong University of Science and Technology, December 21, 2017.
- Cybersecurity Dynamics: Recent Progresses. Wuhan University, December 20, 2017.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. SouthWest JiaoTong University, December 18, 2017.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. East China Normal University, December 13, 2017.
- PD & MTD Dynamics. ARO Invitational Workshop on Foundations and Challenges for Proactive and Dynamic Network Defense, Nov. 30-Dec. 1, 2017, Tampa, USA.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. The 1st International Symposium on Cybersecurity Dynamics, July 19-21, Chongqing University, China.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. School of Computer Science, HuaZhong University of Science and Technology, July 18, 2017.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Hong Kong University of Science and Technology, July 13, 2017.
- Cybersecurity Dynamics: A Foundation for the Science of Cybersecurity. Hong Kong PolyTech University, July 12, 2017.
- Three Case Studies of Metrics and Measurements in the STRAM Framework. ARL, December 13, 2016.
- New Progress in Cybersecurity Dynamics. Institute of Information Engineering, Chinese Academy of Sciences, July 22, 2016.
- New Progress in Cybersecurity Dynamics. School of Computer Science, Huazhong University of Science and Technology, July 19, 2016.
- Towards Eliminating the Threat of Drive-By Download Attacks. School of Mathematics, Fudan University, July 14, 2016.
- New Progress in Cybersecurity Dynamics. School of Mathematics, Fudan University, July 13, 2016.
- Cybersecurity Dynamics. Cyber Security Winter School, Deakin University, July 7-8, 2016.
- Cybersecurity Dynamics. Department of Statistics, University of Science and Technology of China, June 26, 2016.
- A Call for a Theory of Uncertainty in the Cyber Security Domain. Presented at the 2016 Workshop on Mathematical Reliability and Safety, Jiangsu Normal University, China, June 23-25, 2016.
- Cybersecurity Dynamics, Department of Computer Science, University of South Florida, April 7, 2016.
- Grey-Box Cybersecurity Data Analytics. USAF RATPAC Working Group, April 6, 2016.
- Complexity and Network Sciences Support for the Emerging Science of Cyber Security: Challenges and Exciting Research Opportunities. The Minisymposium on Complex Networked Systems: Modeling and Dynamics, the 8th International Congress on Industrial and Applied Mathematics (ICIAM’15), Beijing, China, August 10-14, 2015.
- Cybersecurity Dynamics. School of Computer Science, Fudan University, August 3, 2015.
- Cybersecurity Dynamics. Institute of Information Engineering, Chinese Academy of Sciences, July 21, 2015.
- Cybersecurity Dynamics. Department of Computer Science, Nanjing University, July 16, 2015.
- Cybersecurity Dynamics. Department of Computer Science, George Mason University, June 16, 2015.
- Cyber Defense C2 for Optimizing MTDs. AFRL, June 9, 2015.
- Towards Eliminating the Threat of Drive-By Download Attacks. Department of Mathematics, Illinois State University, April 20, 2015.
- Cybersecurity Dynamics. Department of Mathematics and Computer Science, Clarkson University, April 16, 2015.
- Cybersecurity Dynamics. School of Mathematics, Fudan University, Dec. 18, 2014.
- Cybersecurity Data Analytics. Institute of Information Engineering, Chinese Academy of Sciences, Dec. 16, 2014.
- Cybersecurity Dynamics. Institute of Systems Science, Academy of Mathematics and Systems Science, Chinese Academy of Sciences, Dec. 15, 2014.
- Cybersecurity Data Analytics. School of Software, East China Normal University, Dec. 12, 2014.
- Cybersecurity Dynamics: with application to formulating cyber defense C2 framework. ARO workshop on “Cyber Security: From Tactics to Strategies and Back” held at University of North Carolina at Chapel Hill, Sept. 23, 2014.
- Cybersecurity Dynamics: a foundation to the science of cybersecurity. Keynote at CTCIS’14.
- Towards Orchestrating Moving Target Defense with Quantified Mission Assurance, AFRL, August 26, 2014.
- Cybersecurity Data Analytics. School of Mathematics, Jiangsu Normal University, July 28, 2014.
- Cybersecurity Data Analytics. School of Computer Science, Wuhan University, July 16, 2014.
- Cybersecurity Dynamics. School of Computer Science, Huazhong University of Science and Technology, July 15, 2014.
- Cybersecurity Dynamics. Department of Computer Science, University of North Carolina at Chapel Hill, April 10, 2014.
- Cybersecurity Dynamics. Invited Talk at Inscrypt’13, Nov. 27 – Nov. 30, 2013.
- Cybersecurity Dynamics. Department of Computer Science, University of California at Irvine, Nov. 1, 2013.
- Cybersecurity Dynamics. Department of Electrical Engineering, Arizona State University, Oct. 30, 2013.
- Cybersecurity Dynamics. Department of Computer Science, Texas State University, Oct. 4, 2013.
- Cybersecurity Dynamics. Department of Electrical Engineering and Computer Science, Syracuse University, Sept. 25, 2013.
- Cybersecurity Dynamics. Department of Computer Science, IUPUI, Oct. 12, 2012.
- Toward a Statistical Framework for Using Darkspace-Based Unsolicited Traffic to Infer Cyber Threats, The First International Workshop on Darkspace and Unsolicited Traffic Analysis (DUST’12), May 14-May 15, 2012.
- In Quest of a Foundation for Cyber Security. Department of Computer Science, Texas A&M University, Dec. 1, 2010.
- (How) Can We Manage the Trustworthiness of Security Infrastructures and Services, Keynote address at The 3rd Asia-Pacific Trusted Infrastructure Technologies Conference (APTC 2008), Oct. 14-17, 2008.
,
Acknowledgement. I thank Dr. Moti Yung for mentoring me in the wonderful field of Cryptography — the transformation from the art of cryptography to the science of cryptography has served as the biggest inspiration for this endeavor — and for constantly encouraging me when this endeavor hits road blockers. I thank Dr. Ravi Sandhu for explaining me his model-architecture-mechanism way of thinking. My interactions with them as well as Dr. Elisa Bertino and Dr. Gene Tsudik have, in one way or another, influenced my way of thinking. I have benefited a lot from my interactions with Dr. Steven King, Dr. Alexander Kott, Dr. John McLean, Dr. Sukarno Mertoguno, Dr. Tom Moyer, Dr. David Nicol, Dr. Mike Reiter, Dr. Ananthram Swami, and Dr. Cliff Wang. Their insightful questions/comments have directly deepened my understanding of the problem, and have even led to some exciting future research directions. I thank my mathematician/physicist/statistician collaborators: Dr. Gaofeng Da, Dr. Yujuan Han, Dr. Zi-Gang Huang, Dr. Ying-Cheng Lai (as well we his students), Dr. Xiaohu Li, Dr. Wenlian Lu (as well as his students), Dr. Yilun Shang, Dr. Jie Sun, and Dr. Maochao Xu. My collaboration with them has made me understand better the strengths and limitations of several Applied Mathematics techniques (broadly defined) in coping with the problems encountered in this endeavor. I thanks all of my co-authors for the fruitful collaboration.
This research endeavor has been supported in part by ARO, ARL, AFOSR, AFRL, DOE, NSA, NSF, and ONR.
Created: 9/2/2013; Last edited: 12/25/2022